Shocking Details About What Is Anti Spoofing In Firewall Instructed By An Skilled
Website spoofing is a scam where cyber criminals create a website that intently resembles a trusted brand in addition to a site that’s virtually identical to a brand’s net area. As a result of the scam taking place exterior of a company’s security perimeter, website spoofing is usually only uncovered after several users have already fallen prey to the attack. Block and take down each active scam and suspicious website within the early phases of an assault. Take rapid motion to stop active scams and block suspicious domain names and urls. Protect your workers, prospects, and companions from phishing scams that use domain names and websites like yours to scouse borrow cash, facts, and identities. In this case, you merely use the true host’s IP address as the next hop.
Mimecast addresses this downside with model protection solutions that use machine learning and net scans to determine suspicious domains and cloned sites, blocking them before they launch or stopping dwell assaults in their tracks. A brand can pick out even unknown attack patterns and block compromised belongings at the earliest preparation stages – earlier than they change into stay attacks. To stop website spoofing, this Mimecast Model Exploit Protect uses machine studying to run quadrillions of targeted scans, trying to find domains like yours and websites that may be spoofing yours. Mimecast model exploits protect obtainable as a saas/cloud-based mostly service that may be applied quickly to start defending your model instantly. Even unsophisticated attackers can register a site that is very near the area of a trusted model and construct a site that looks identical to the model’s website https://antispoofing.org/.
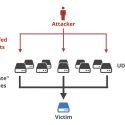
Then, using phishing emails, attackers can lure the brand’s customers, partners, and others to the location and trick them into revealing delicate data like bank card numbers, Social Security numbers, or login credentials. The objective of website spoofing is to lure a brand’s clients, suppliers, partners, and employees to a fraudulent website and convince them to proportion sensitive information like login credentials, Social Safety numbers, bank card data, or checking account numbers. It might also order an employee to make a financial institution transmission of a considerable sum of money. A sufferer might be a traditional host, e.g., a Computer or Notebook, gateway, or perhaps a router! Or, the spoofed e-mail might appear to be coming from one of the victim company’s companions, whereas the truth is, it is despatched by the attacker.


